Hey folks, long time no write!
Today I want to bring a tip that I use every week but I found that most SSMS users are unaware it exists.
I can understand why! At the moment this isn’t the most obvious and user-friendly option. However, it can and hopefully it will improve in the future.
“But…What is it?”
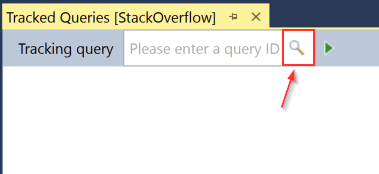
I’m talking about using the Query Store GUI to search for some portion of text used in a T-SQL query and, with that, find a query that you want to analyze within it.